Safeguarding Protected Health Information (PHI): Preparing for the Onslaught
-
October 19, 2022
-
Private equity investment in healthcare has nearly tripled during the past decade, increasing from $41.5 billion in 2010 to $119.9 billion in 2019.1 This investment reflects the large size of the market, its prospects for growth driven by aging demographics and opportunities for leverage via economies of scale. Coincident with increased investment has been a concomitant rise in data breaches, inclusive of ransomware (which accounts for one-third of attacks).2
The U.S. Department of Health and Human Services (HHS) defines a data breach as “an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the protected health information.”3 The Privacy Rule protects “individually identifiable health information.”4
The frequency of healthcare data breaches, magnitude of exposed records, and financial losses due to breached records have increased rapidly during the past few years.5
Between 2005 and 2019, there were 6,355 data breaches of which 3,912 were in healthcare (61.55%).6 Breaches involving the loss of 500 or more records (642 in 2020 and 712 in 2021) continue to increase.7 The first half of 2022 showed a decline of 5.71% compared to the prior year, though the decline is believed to be related to a delay in reporting8 Providers, health plans and business associates reported that approximately 20.2 million records were breached in 1H22.9
One notable breach, a ransomware attack on HIPAA business associate Professional Finance Company, affected 657 HIPAA-covered entities.10
Number of healthcare data breaches involving the loss of 500 or more records in the United States 2009 to 2021
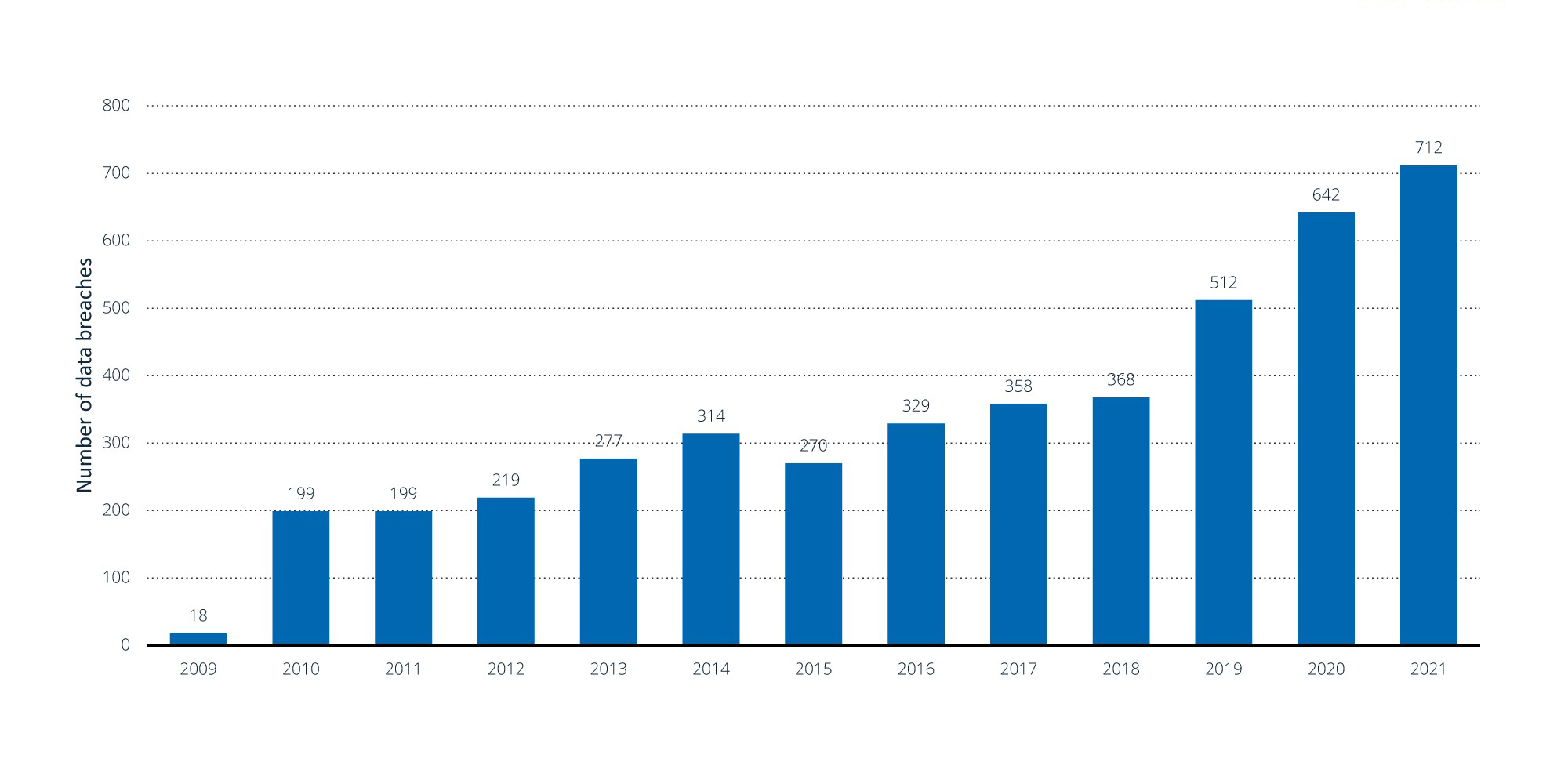
Note(s): United States; 2009 to 2021; data breaches involving the loss of 500 or more records
Further information regarding this statistic can be found on page 8.
Source(s): HIPAA Journal; ID 1274594
Hacking is the most common cause of a data breach, followed by unauthorized internal disclosure.11 External remote services such as remote desktop protocol and virtual private networks are being targeted.12 In 2019, PHI breached locations include email (37.8%), network servers (22.2%), paper/films (11.0%), electronic medical records (7.4%) and other sources (21.6%).13 A more recent study from the first half of 2022 suggests network servers (55.2%) and email (26.0%) account for the preponderance of PHI breached locations.14 The average cost of a healthcare data breach is $9.23 million.15
In this article, we create a risk assessment framework and provide guidelines for cybersecurity resilience and incident response. Opportunities exist to proactively assess vulnerabilities and minimize risks.
Strategies Prior to a Breach
With the unprecedented rise of data breaches from the rapidly evolving sophistication of ransomware attacks, an increasing number of organizations are realizing that it is nearly impossible to prevent the consequences of all attacks. Instead, they are focusing their attention on minimizing the likelihood of a data breach and, in the event of a successful attack, how they can quickly resume operations of critical organizational processes, systems and operations with minimal loss of data and impact to the organization.
Strategically, healthcare organizations should consider developing a comprehensive cybersecurity risk management program at the enterprise level and ensure cybersecurity buy-in from executive leaders and the board in order to drive a culture of security awareness across the organization.
Tactically, organizations should consider performing periodic vulnerability assessments and pen tests, ensure a patch management cadence, encrypt ePHI and other sensitive data at rest and, where applicable, data in transit, and regularly test their incident response, back-up and business continuity planning/disaster recovery plans.
Post-Breach Strategies
As part of their incident response strategy, firms should consider:
- engaging in corporate risk and resiliency planning to quickly bounce back from disruptions
- understanding the vulnerabilities based on pre-breach assessments; assess the potential impact of a breach to become more prepared to handle it rapidly and with minimal damage
- identifying adverse events in computerized networks to defend against, detect and remediate threats
- utilizing a threat-intelligence approach to cybersecurity in order to identify and respond to threats quickly
- continually revisiting and updating response plans as new cyber threats emerge and evolve
The implications of not having an up-to-date incident response strategy include damage to a firm’s reputation, a loss of customer trust, and a loss of revenue from an extended period of inaccessible systems caused by slow incident response.
Firms can minimize risks related to business associates by:
- performing business associate due diligence prior to onboarding to ensure associates have appropriate administrative, technical and physical controls in place to safeguard confidentiality, availability and integrity of ePHI (inclusive of the associates’ third parties)
- executing business-associate agreements with all applicable parties prior to the exchange of ePHI
- periodically assessing risks related to business associates based on criticality of services provided and type of data (e.g., ePHI) exchanged, and having a documented remediation plan where needed
Cybersecurity-Compliance Divide
Considerations for firms when closing the gap between compliance and security:
- National standards for cybersecurity compliance, such as SOX, HIPAA, HITRUST, PCI, CIS and NIST, frequently revise their guidelines to stay on top of the latest cyber threats facing the healthcare industry. For example, NIST, the National Institute of Standards and Technology, released an updated draft of healthcare cybersecurity guidance in July 2022, focused on providing resources to help organizations comply with HIPAA and protect PHI and ePHI.16 Following this framework can help firms ensure compliance to national standards.
- There are risks confronting businesses that do not comply with these regulations, as compliance can be evidenced: Litigation following a cybersecurity incident usually focuses on whether a firm was following national cyber standards, so compliance can protect a firm from legal consequences if a breach does occur.
- However, compliance to regulations serves as a minimum threshold for cybersecurity, and firms cannot rely on compliance alone to protect them from a cyberattack. Compliance does not equal security, and security does not equal secure; therefore, make sure teams understand the differences to be able to develop a process of implementing controls for threat intelligence in addition to compliance.
- Take a multidisciplinary approach to bringing people across the organization to focus on security together so that ePHI remains protected across financial and HR systems along with healthcare systems.
- Develop a governance, risk and compliance framework that addresses how standards and legislation are adhered to; simply stopping with compliance will not keep a firm safe from cyber incidents.
- Consider a security program that operates threat-based controls: While regulation compliance is a good start, that alone will not keep a firm safe from cyber threats. These standards are meant to apply to a broad range of organizations, so each firm must also consider threats unique to the firm to identify and stop threats before they happen.
Bottom line
Cybersecurity has emerged as essential to “protecting networks, devices, and data from unauthorized access or criminal use” and of “ensuring confidentiality, integrity, and availability of information.”17
Large scale data breaches have doubled in the past five years; tens of millions of records were involved. Breach costs have also increased. Data breaches may not only occur at a provider, but also at a business associate.
Opportunities exist to reduce risk. Compliance, by itself, is not enough. Resilience testing can be used to assess vulnerabilities and simulate potential attacks. Cybersecurity efforts also involve post-breach activities to minimize impact. FTI Consulting can assist in these activities.
Footnotes:
1: Richard M. Scheffler, Laura M. Alexander, and James R. Godwin. “Soaring Private Equity Investment in the Healthcare Sector: Consolidation Accelerated, Competition Undermined, and Patients At Risk.” American Antitrust Institute, and Petris Center School of Public Health, University of California Berkely (May 18, 2021). https://publichealth.berkeley.edu/wp-content/uploads/2021/05/Private-Equity-I-Healthcare-Report-FINAL.pdf.
2: Jessica Kim Cohen. “Ransomware attack at RCM vendor hits 942k patients’ data.” Modern Healthcare (August 17, 2022). https://www.modernhealthcare.com/cybersecurity/practice-resources-reports-breach-affecting-942k-patients.
3: Health Information Privacy. “Breach Notification Rule.” HHS.gov, U.S. Department of Health & Human Services (last visited August 16, 2022). https://www.hhs.gov/hipaa/for-professionals/breach-notification/index.html.
4: Health Information Privacy. “Summary of the HIPAA Privacy Rule.” HHS.gov, U.S. Department of Health & Human Services (last visited August 16, 2022). https://www.hhs.gov/hipaa/for-professionals/privacy/laws-regulations/index.html.
5: Laurie Iocono, Heith Wojcieszek, and George Glass. “Q2 2022 Threat Landscape: Ransomware Returns, Healthcare Hit
6: Adil Hussain Seh, et al. “Healthcare Data Breaches: Insights and Implications.” Healthcare (Basel) (May 13, 2020). https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7349636/.
7: Statista sourced from HIPAA Journal https://www.statista.com/statistics/1274594/us-healthcare-data-breaches/
8: “1H 2022 Healthcare Data Breach Report.” HIPAA Journal (August 11, 2022). https://www.hipaajournal.com/1h-2022-healthcare-data-breach-report/.
9: Ibid.
10: Ibid.
11: Adil Hussain Seh, et al. “Healthcare Data Breaches: Insights and Implications.” Healthcare (Basel) (May 13, 2020). https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7349636/
12: Laurie Iacono, Keith Wojcieszek, and George Glass. “Q2 2022 Threat Landscape: Ransomware Returns, Healthcare Hit.” Kroll Cyber Risk (August 10, 2022). https://www.kroll.com/en/insights/publications/cyber/q2-2022-threat-landscape-ransomware-healthcare-hit.
13: Adil Hussain Seh, Mohammad Zarour, Mamdouh Alenezi, Amal Krishna Sarkar, Alka Agrawal, Rajeev Kumar, and Raees Ahmad Khan. “Healthcare Data Breaches: Insights and Implications.” Healthcare (Basel). (May 13, 2020). https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7349636/
14: “1H 2022 Healthcare Data Breach Report.” HIPAA Journal. (August 11, 2022). https://www.hipaajournal.com/1h-2022-healthcare-data-breach-report/
15: Drew Todd. “Ponemon Institute: Cost of Data Breach Hits Record High.” SecureWorld. (September 1, 2021) https://www.secureworld.io/industry-news/cost-of-a-data-breach
16: “NIST Updates Guidance for Health Care Cybersecurity.” National Institute of Standards and Technology, U.S. Department of Commerce (updated September 20, 2022). https://www.nist.gov/news-events/news/2022/07/nist-updates-guidance-health-care-cybersecurity.
17: “Security Tip (ST04-001): What is Cybersecurity?” Cybersecurity & Infrastructure Security Agent (revised November 14, 2019). https://www.cisa.gov/uscert/ncas/tips/ST04-001.
© Copyright 2022. The views expressed herein are those of the author(s) and not necessarily the views of FTI Consulting, Inc., its management, its subsidiaries, its affiliates, or its other professionals.
Related Insights
Related Information
Published
October 19, 2022
 Key Contacts
Key Contacts
Managing Director
Most Popular Insights
- Beyond Cost Metrics: Recognizing the True Value of Nuclear Energy
- Finally, Pundits Are Talking About Rising Consumer Loan Delinquencies
- A New Era of Medicaid Reform
- Turning Vision and Strategy Into Action: The Role of Operating Model Design
- The Hidden Risk for Data Centers That No One is Talking About


